Rapid7 - insightVM
Lightweight Endpoint Agent
The Rapid7 Insight Agent automatically collects data from all your endpoints, even those from remote workers and sensitive assets that cannot be actively scanned, or that rarely join the corporate network.
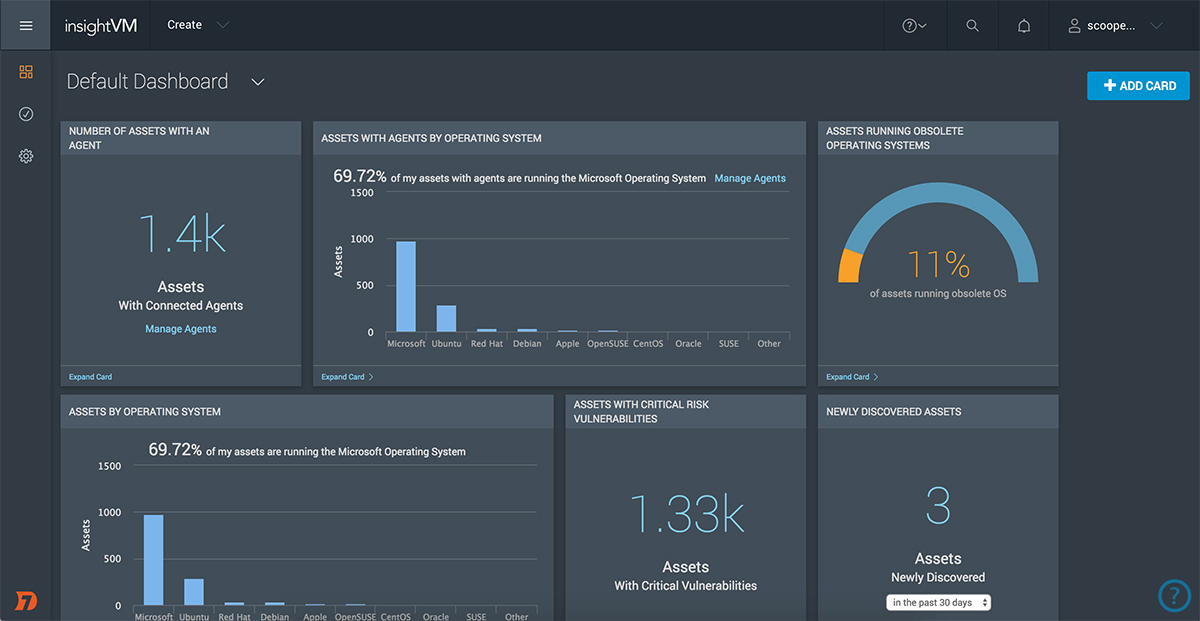
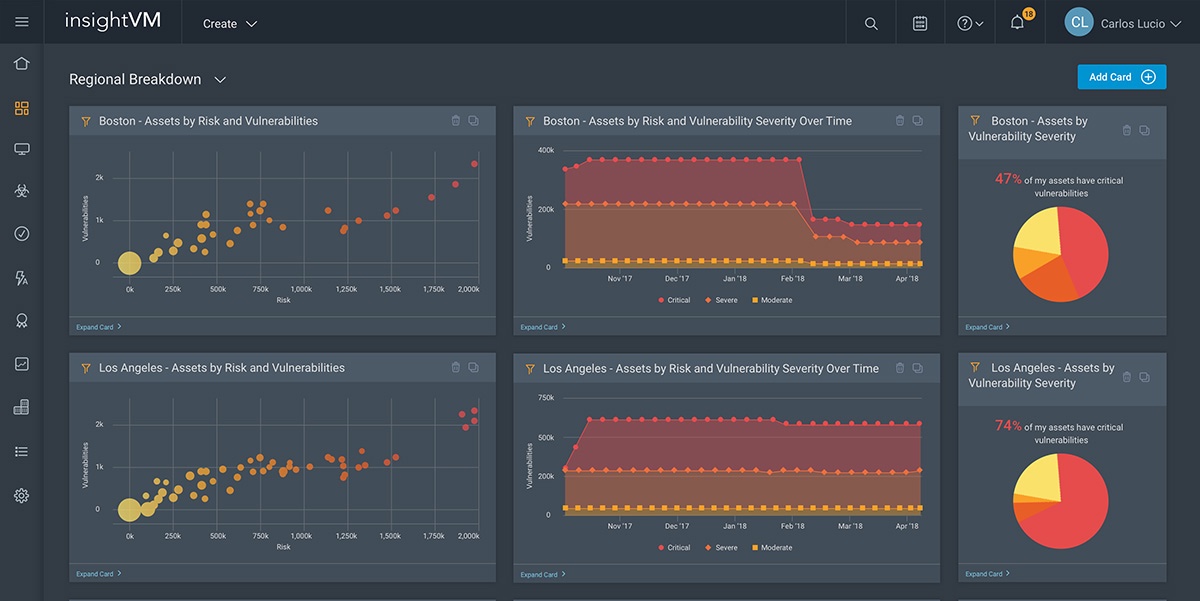
Live Dashboards
Most software dashboards are static: a snapshot of your risk at a particular time, unclickable and instantly out of date. InsightVM Live Dashboards are live and interactive by nature. You can easily create custom cards and full dashboards for anyone—from system admins to CISOs—and query each card with simple language to track progress of your security program.
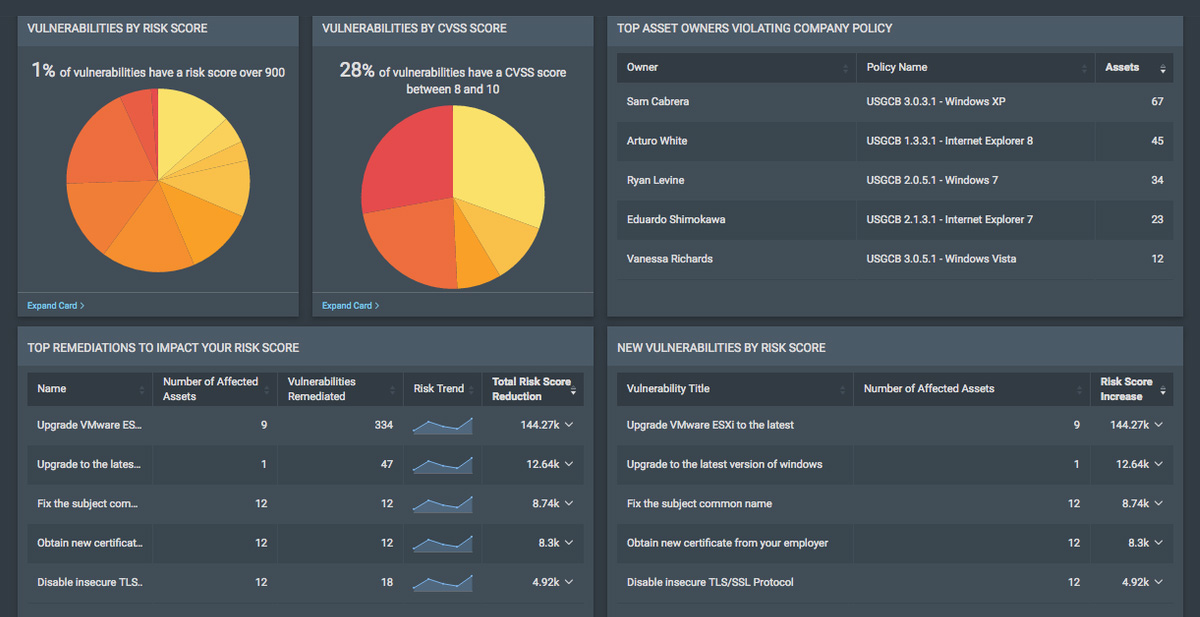
Real Risk Prioritization
CVSS-based risk scores result in thousands of "critical" vulnerabilities. No business, even one with an army of analysts, has the time for that. Our Real Risk Score provides a more actionable, 1-1000 scale based on the likeliness of an attacker exploiting the vulnerability in a real attack. Backed up by threat feeds and business context, InsightVM lets you prioritize vulnerabilities the way attackers would.
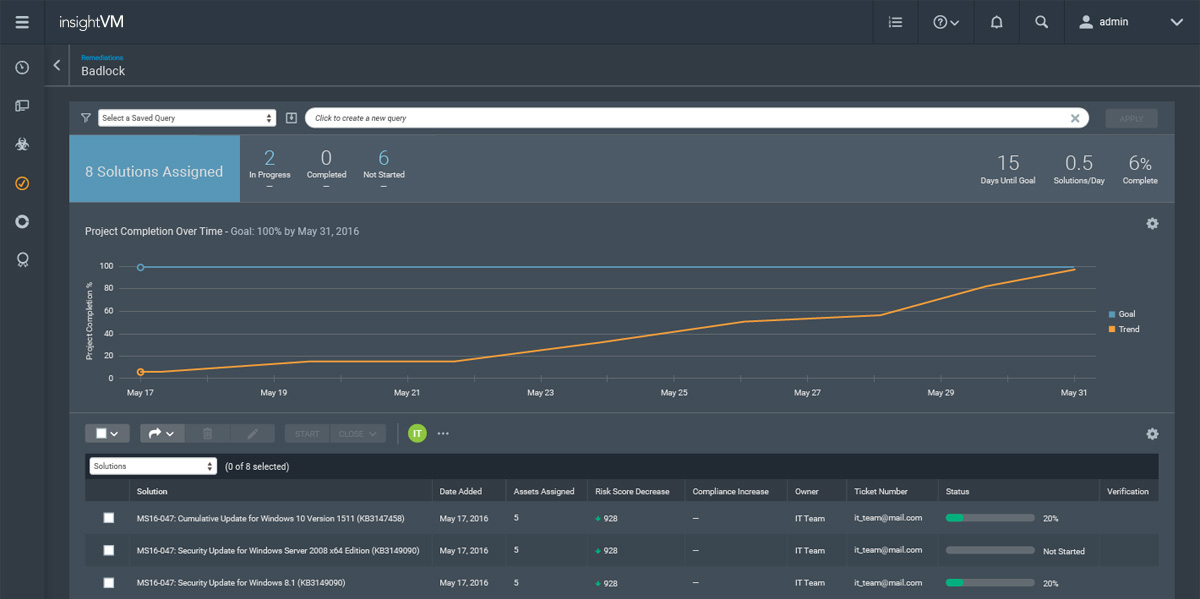
IT-Integrated Remediation Projects
Trash the thousand-page remediation reports, complex spreadsheets, and confusing back-and-forth email tag. With Remediation Projects, security teams can assign and track remediation duties in real time, providing continuous visibility into how well issues are being fixed. Take it one step further by integrating InsightVM directly with IT's ticketing systems to fold remediation seamlessly into their daily workload.
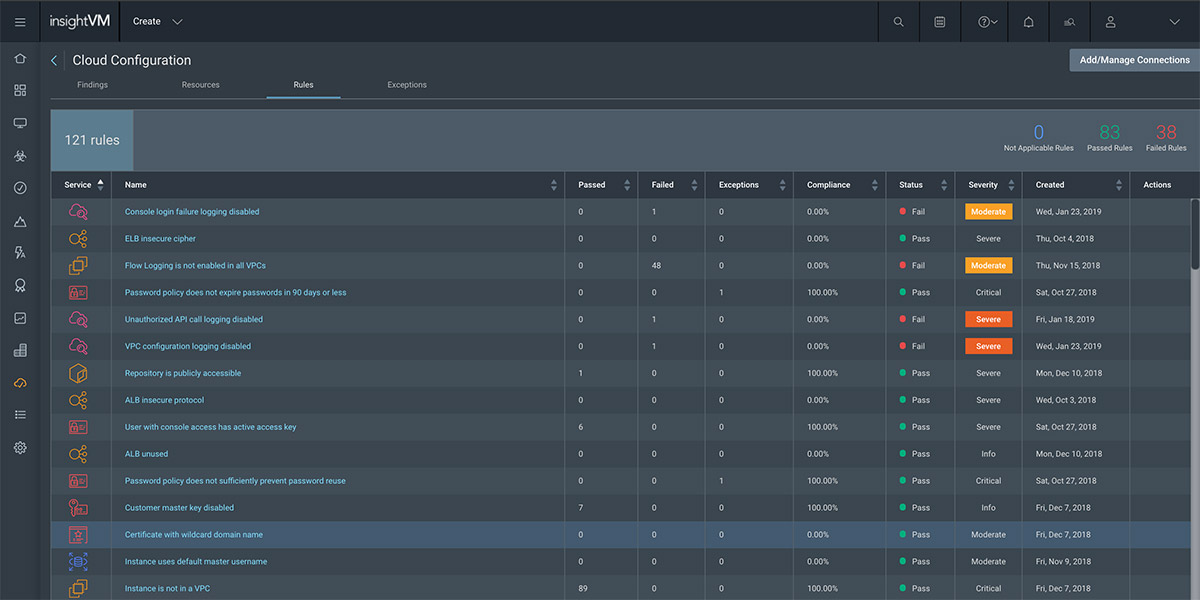
Cloud and Virtual Infrastructure Assessment
"The severity scoring of findings [in InsightVM Cloud Configuration Assessment] has helped out a lot to drive prioritization of what to fix."
— Jason Hughes, Senior Cloud Security Engineer at Origami Risk
Modern networks and infrastructures are constantly changing. InsightVM integrates with cloud services and virtual infrastructure to make sure your technology has been configured securely, and that you don't miss any new devices that are brought online. The gist of it all? You get full visibility into risk across your physical, virtual, and cloud infrastructure.
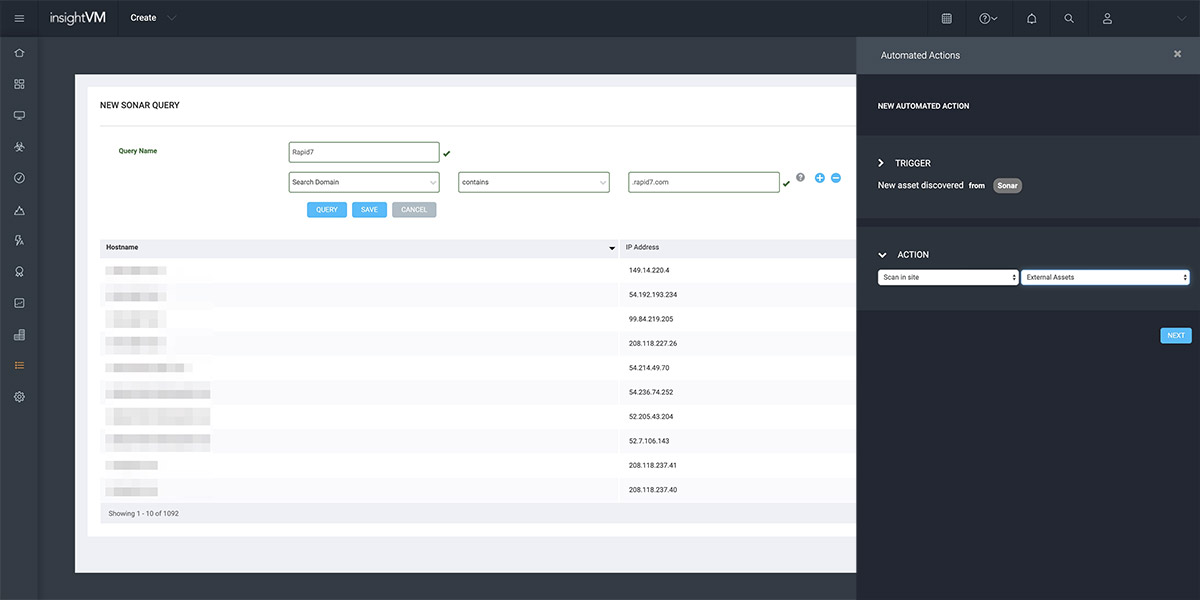
Attack Surface Monitoring with Project Sonar
As your organization grows and your infrastructure becomes more complex, maintaining visibility into your changing attack surface becomes more challenging. InsightVM directly integrates with Project Sonar, a Rapid7 research project that regularly scans the public internet to gain insights into global exposure to common vulns. By leveraging Attack Surface Monitoring with Project Sonar, you can be confident that you have a pulse on all of your external-facing assets, both known and unknown.
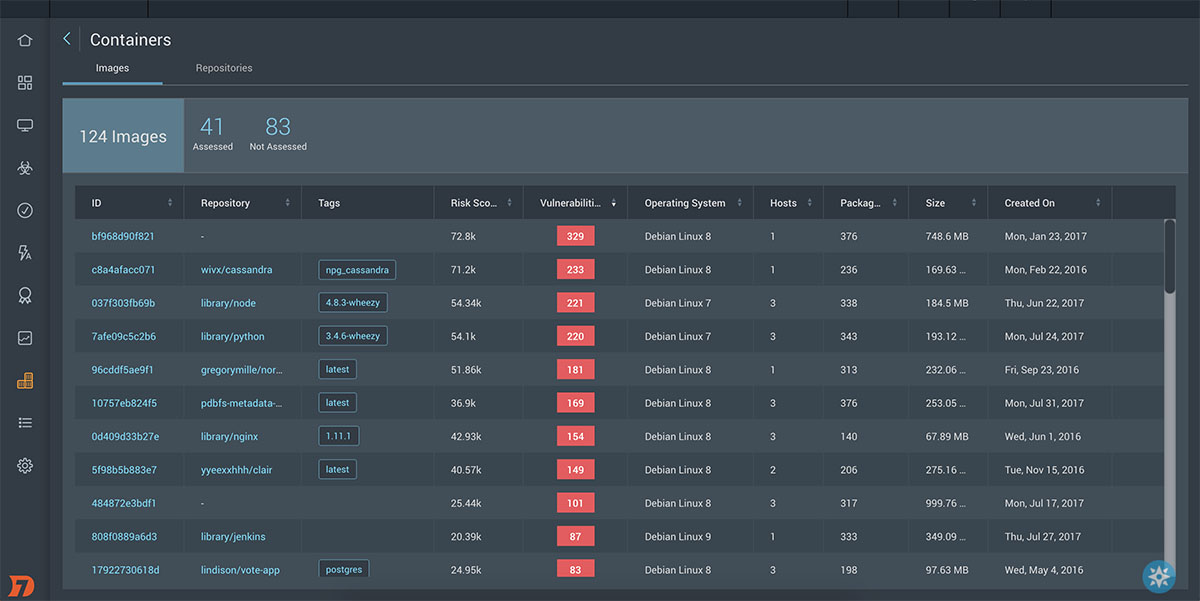
Container Security
InsightVM integrates with your CI/CD tools, public container repositories, and private repositories to assess container images for vulnerabilities during the build process—before they're deployed. Need to identify containers in your environment? Discover and correlate deployed containers to assets, so you can then secure both containers and their hosts.
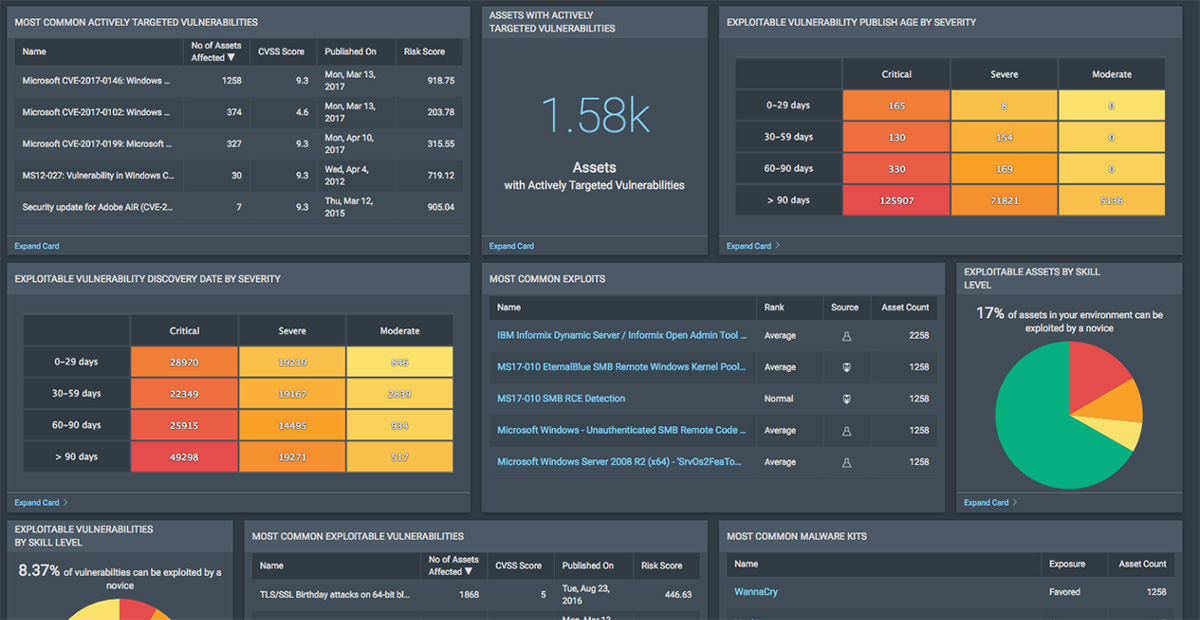
Integrated Threat Feeds
"The threat feeds in InsightVM let me sort through the noise of other "high" severity vulnerabilities with low probability of exploitation, and go straight to the vulns that matter—the ones that are actively targeted by attackers."
— Chad Kliewer, Information Security Officer at Pioneer Telephone
Leverage our researchers' insights into the threat landscape and recent attacker methods with complimentary Threat Feeds in InsightVM. This dynamic view shows you the threats that are most relevant to your environment, enabling you to better protect against current, impending threats and react quickly to critical, named vulnerabilities.
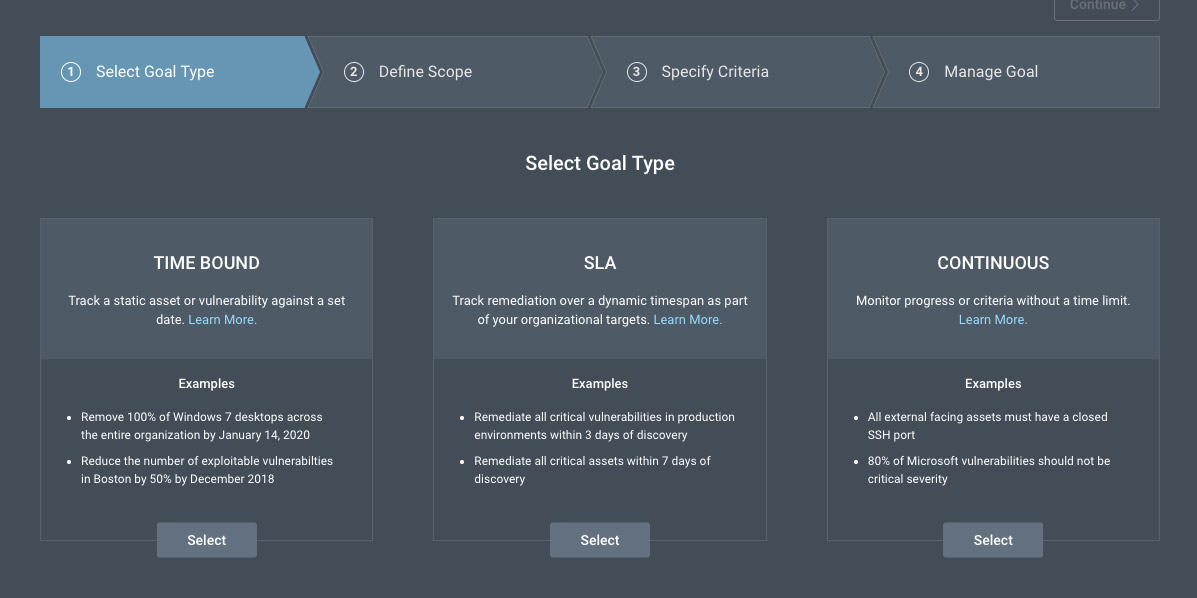
Goals and SLAs
Between the notifications of high criticality vulns and back-and-forth email communications that frequently come with vulnerability assessment, we don't often get to ask ourselves, "what is the true effectiveness of my vulnerability management program?" This question becomes increasingly difficult to answer when the completion of remediation tasks spans multiple teams and projects. This is where Goals and SLAs come in.
With Goals and SLAs, you can ensure that you're making (and tracking) progress toward your goals and service level agreements (SLAs) at an appropriate pace, and maintaining compliance with the standards you've set for your program.
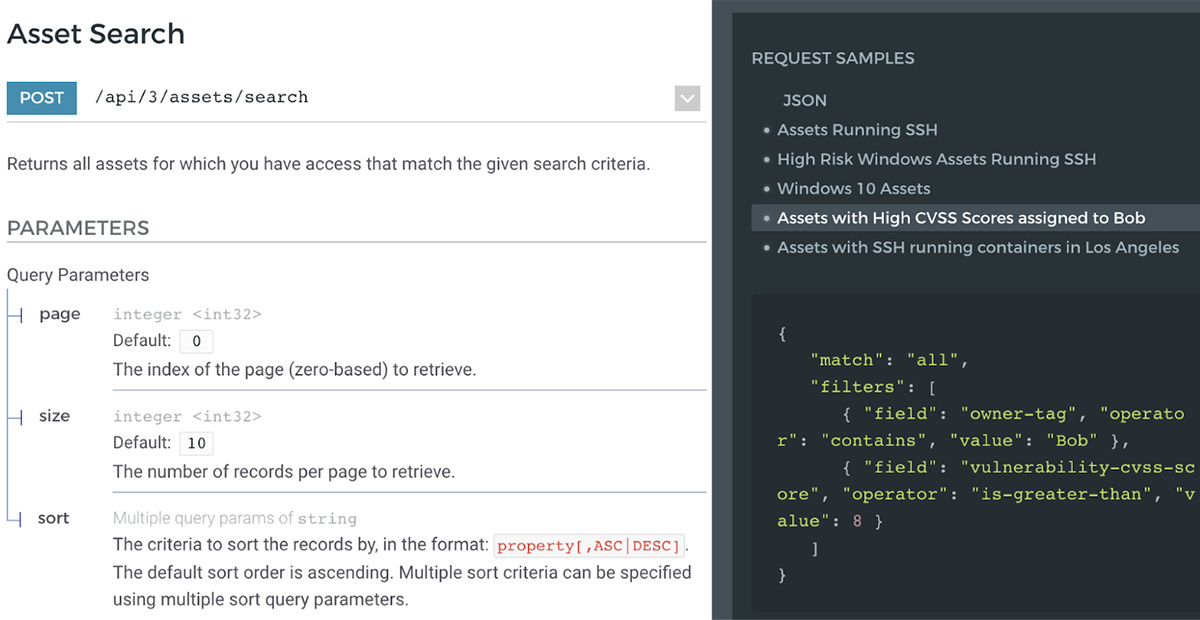
Easy-to-Use RESTful API
Your team should have the power to take control of your Security Console, not the other way around. InsightVM's RESTful API makes it (almost ridiculously) simple to accomplish more within your unique security program. It was built to easily automate virtually any aspect of vulnerability management, from data collection to risk analysis, and integrate InsightVM capabilities with your other processes.
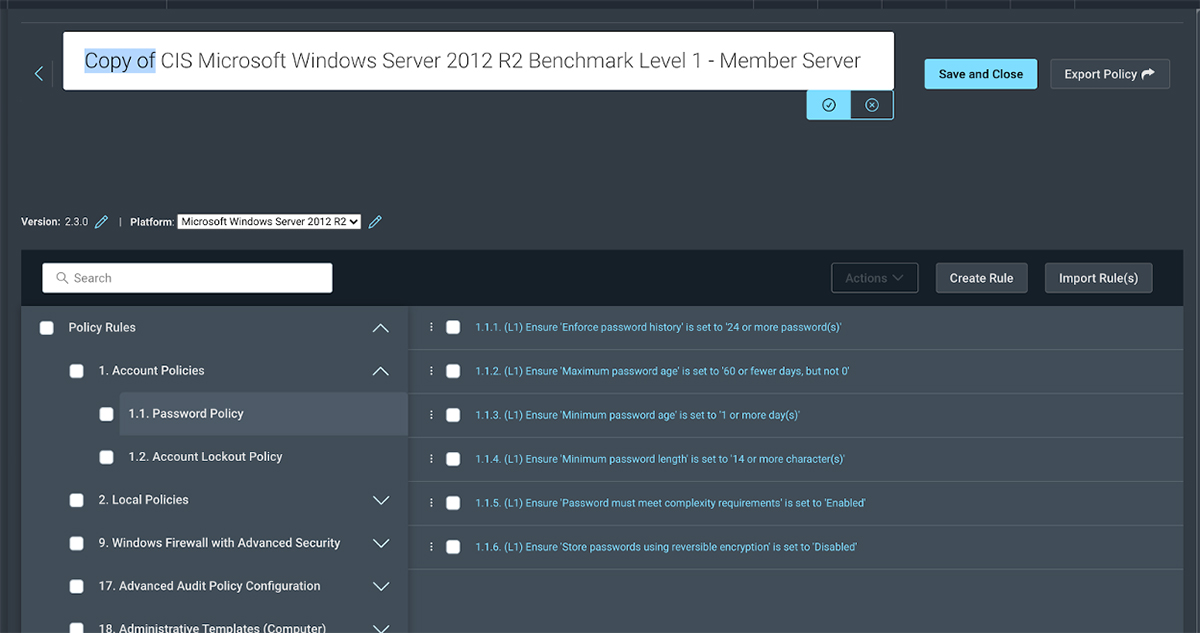
Policy Assessment
Beyond your own internal security goals, we know many organizations are also accountable for compliance to various security policies and standards. InsightVM eases this process by offering pre-built scan templates for common compliance requirements. Once you've assessed your risk posture, you can take clear, actionable steps to compliance. To go a step further, Custom Policy Builder allows you to modify existing benchmarks or create new policies from scratch to meet the needs of your unique operating environment.
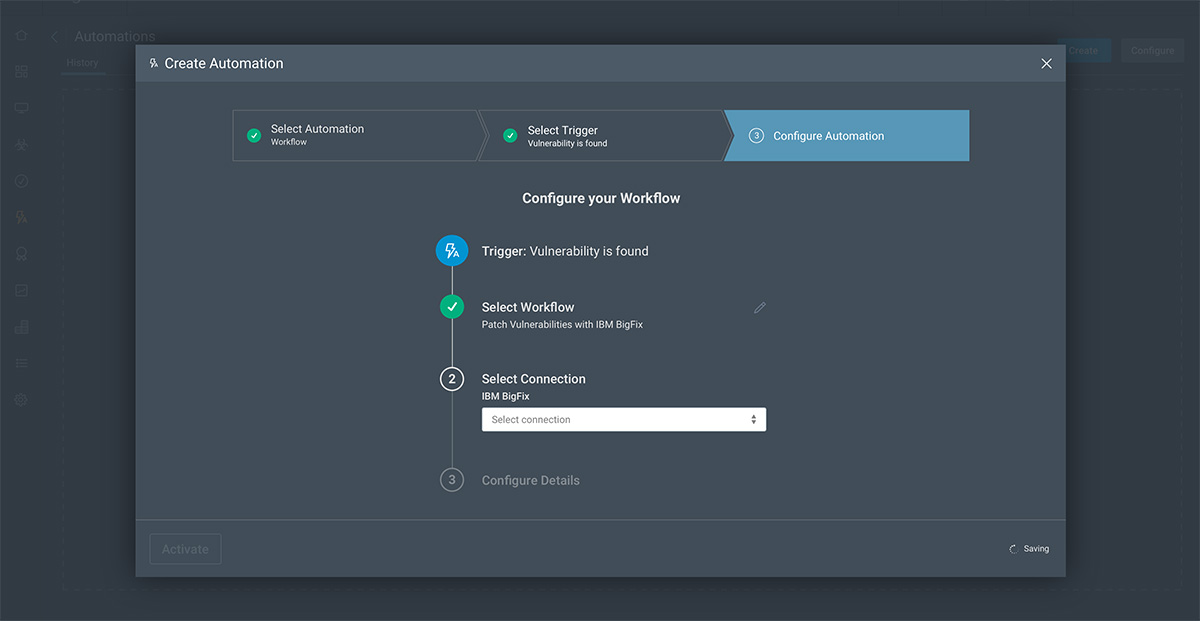
Automation-Assisted Patching
Leverage your people and resources most efficiently by streamlining remediation, a traditionally tedious and time-consuming task. Automate the steps of aggregating key information, retrieving fixes for identified vulnerabilities, and ultimately—when appropriate and/or approved by a sysadmin—applying the patches. Upon completion, you can have InsightVM automatically re-assess impacted assets to verify successful patching. This way, you can stop worrying about the mundane and repetitive aspects of your job, and refocus your efforts toward a larger vulnerability management strategy.
Automated Containment
It’s the hard truth: You can’t remediate every vulnerability you find immediately—or maybe ever. With Automated Containment, you can decrease exposure from these vulnerabilities by automatically implementing temporary (or permanent) compensating controls via your Network Access Control (NAC) systems, Firewalls, and Endpoint Detection and Response tools; these can act as both stopgaps or long term solutions to reduce exposure.
لم يتم العثور على أي تقييمات